BLOG
Customer Story | Meals on Wheels SA centralises IT to realise $50,000 cost saving
Meals on Wheels SA centralises its IT environment to better coordinate thousands of daily deliveries. Almost everyone has heard of Meals on Wheels. David explained that implementing an Intelligent Information Management System allowed his group to digitise their financial model, saving his business $50K per year while increasing efficiency and security.
Meals on Wheels SA centralises its IT environment to better coordinate thousands of daily deliveries
Almost everyone has heard of Meals on Wheels. It was first formed in South Australia (SA), in 1954. Founder Doris Taylor MBE, wheelchair-bound from an accident as a teen, empathised with the challenges of those returning home from the hospital. She noted, in the elderly in particular, that they had trouble shopping and preparing meals for themselves, often depriving them of the ability to live independently. Meals on Wheels was her remedy. Nearly seventy years on, more than 50 million meals have made their way into SA homes. The organisation is currently providing 4,300 meals per day to customers across the state.
Key Challenges
The state-wide operation included a vast degree of variation among branches
There was no single payments system and accounting was resource-intense
COVID-19 caused a surge in demand that could only be met by a centralised model
In every other Australian state, Meals on Wheels operates as several independent entities. However, Meals on Wheels SA is a state-wide association with 80 branches. Some were established under the state-wide model, while others were independent organisations incorporated into the association - the latter managed their own affairs, with committees, treasurers, bank accounts and chequebooks. Add to this that many pre-dated the internet, set up without the benefit of computerised systems, and you get an idea of the variation within the Meals on Wheels model.
Even so, it’s a model that has served the community well for 50 years. Testimony to its success is the tenure of its volunteers. Among seven thousand volunteers, the average age is 75. David Smith, Executive Manager, Corporate Services for Meal on Wheels, recalls the first time he attended an annual award ceremony recognising long term volunteers; “There were 40 people who had been volunteering for 40 years,” he says.
COVID-19 caused a surge in demand
When COVID-19 arrived in early 2020, hitting Australian businesses hard, Meals on Wheels wasn’t one of them. “Quite the opposite,” Smith says. A surge in demand for meal services presented the organisation with the challenge of meeting it with maximum efficiency.
Growing fast in a controlled way required digitising and automating financial processes. It also called for complete compliance with Work health and safety (WHS) standards which view volunteers as employees, governed by the same safety rules. This includes 75 to 90-year-old volunteers who'd never had to think about them before during their working lives. “They've always stood on a ladder on top of a table to change a light bulb, so why would they not do it now?” says Smith.
Finally, the model needed to flexibly accommodate digital and non-digital interaction. Any assumption that in time everyone will become comfortable with internet-based services doesn’t take into consideration the aging population. “Just because you are computer literate now, it doesn't mean that when you're 85 or 90 you're somehow going to be magically better. And so this market for people who are getting older, and some of their capacities have diminished, they're always going to need a meal delivered to their house,” says Smith.
Meals on Wheels SA contacted Advance Business Consulting to help them cut through these requirements to arrive at a system that would allow them to grow securely with a fraction of the effort while getting more from their technology and data.
The challenge of connecting everyone
Creating a common organisational infrastructure was a priority. But not every branch had a physical office to call their own, and a few smaller branches had been relying on their own computers to log into Meals on Wheels. Smith leaned on Advance’s consultancy services to design an infrastructure capable of accommodating what Smith refers to as the “lowest common denominator of what you need a computer to be.” In this way, it would be embraced by everyone, regardless of their circumstance.
Security was top of mind. “If you have to put a secure internet connection in a branch and a managed computer, and that computer is only going to be used for one hour, twice a week, it's quite a big investment for a very small use case. Also, you don't know who's going to be using it. It might be 20 different people in a branch,” says Smith, who looked to Advance to propose the most viable security strategy.
Opportunity to streamline payments processes
Digitising and automating payments within one simple payment system was identified as an excellent way to inject efficiency into operations. In the past, Central Office would invoice the branches for meals delivered, and reimburse costs incurred by them. If those costs had been incurred directly by Central Office and not the branch, which sometimes happened, another invoice would be issued for the money to be returned. A reconciliation was completed every three months on a simple electronic cash book, to check the accuracy and retrieve surplus funds advanced but not used. There was also an exercise of distributing funds from more profitable branches to those who needed “propping up” to ensure equity across the model. Accounting in this way took time and resources that Meals on Wheels decided it would prefer to apply to service excellence.
Solutions:
Advance standardised how branches connected to Central Office
World-class security was built in via VPN enabled teleworker devices
M-files automated important processes like payments and reimbursements
One simple means of connecting
Advance migrated Meals on Wheels from Telstra 4g connections to a Cisco Meraki SD-WAN with Teleworker VPN, which has proven to be incredibly successful. Teleworker devices are not carrier dependent, for one thing, which supports the association’s need for flexible connectivity, as well as delivering world-class security. In this model, secure corporate LAN connectivity is extended to employees at remote sites via Meraki APs (access points), without needing them to install VPN software on their devices themselves. It can all be done centrally, keeping things simple.
Added security benefits are realised through Meals on Wheels’ ability to whitelist applications, making them unavailable to users on their devices, as well as best-in-class anti-virus software. This provides better protection from hackers. “Meals on Wheels is a very well-known name, which unfortunately makes us an obvious target for cybercrime,” says David.
A unified payment system
Improving the efficiency of the outgrown payment system began with eliminating the need for branches to pay their own invoices. “How do you get at branches to be able to effectively send invoices into Central Office if they want to send them by fax, which some still do?” says Smith. “But of course, that really just pushes the workload elsewhere.”
Advance suggested M-files, a document management system for coordinating the right information to the right people at the right time. This immediately gave branches the ability to scan an invoice, sign to confirm goods had been received, and be paid automatically. Where branches don’t always have a reliable internet connection, M-files helps with that too: “M-files was great because we could actually fall back to a mobile phone to do the same thing,” says Smith. “And in a couple of cases we still do use the fax, but what it means is no longer needing branches to pay any bills”
Verifying and reimbursing drivers
Additionally, M-files was set up to support driver reimbursement. Volunteers are paid a fee per delivery for their petrol and wear and tear. “They used to be paid in cash. The driver could take the money and if they didn't, it got flipped into a bucket and then banked as a donation,” says Smith. M-files has automated the entire process with a workflow that lets Meals on Wheels collect a declaration from drivers with their bank account details for payment. Stored securely in M-files, it can be centrally and accurately managed.
“We realised while we're doing this, it would be useful to check that the person we're paying a driver reimbursement to is actually a volunteer,” says Smith, explaining that people used to get roped in to be a deliverer and stay for 10 years when they're not actually on the books. If they're not registered, it means they haven't had a police check. “Right through this process, we found little added gains from simply just trying to improve a process,” Smith says.
Compliance is much easier
Driver verification is one aspect of compliance, but it’s not the only one to benefit from the new technology-enabled operational model. Meals on Wheels can now issue communications on things like Work health and safety rules to employees and volunteers with minimum effort and feel confident they have been received.
Outcomes:
Closing the branch bank accounts saves $50,000 per year
New employees can be onboarded, from anywhere, in moments
Centralised management of data drives compliance across 80 branches and 7000 volunteers
When you no longer need to pay for anything by cash or cheque, you don't need money. Meals on Wheels has been able to close all its bank accounts. This simple act is saving of $50,000 per year in bank fees and transaction costs.
Security concerns are alleviated through central controls configured by Advance that let Meals on Wheels whitelist applications and prevent people from running programs that are not supposed to.
The project, which began pre-pandemic, turned out to be well-timed since it allowed Meals on Wheels to rapidly transition to a work-from-home strategy during COVID-19 restrictions with the Meraki teleworking devices. “When our staff had to work from home, it was a trivial matter to give them a network device with a SIM card in and connect them and get them working. It was an accidental benefit that really set us in good stead.”
Since kicking off its transformation, Meals on Wheels SA has gone from strength to strength, most recently introducing a new ERP system, Pronto, for dealing with manufacturing, and other important resources, with efficiency, and creating a host of web applications using low-code development tool Intrexx, provided by Advance.
With the expansion of services no longer a heavy lift, the sky is the limit.
CONTACT US
For any further information regarding how Advance can help implement a successful digital process in your industry, get in touch with us here. We’re here to help!
KEY TECHNOLOGY PARTNERS
Low-code development platform | Intrexx
BI | Power BI and Qlik -BI | Some interesting changes at Qlik and what to look for in a business intelligence solution
At Advance, we work with tools like Qlik and Microsoft Power BI when delivering business intelligence solutions to provide actionable insights for our clients.
At Advance, we work with tools like Qlik and Microsoft Power BI when delivering business intelligence solutions to provide actionable insights for our clients. Both tools are market leaders and each vendor has a slightly different approach in delivering new insights. We wanted to take a look at some recent changes in Qlik’s licencing model that enables a more complete BI solution and our view on areas to consider when looking at BI tools.
Want to know more about BI and some outcomes we have delivered? We are passionate BI experts. Get in touch here.
Why would you want a BI solution?
BI offers new actionable insights into your business and will empower employees, deliver automated, efficient reporting and analytical dashboards. BI offers insights to provide new and improved:
Revenue streams
Customer experiences
Business processes
Competitive insights
Business performance
Collaboration
Unexpected benefits along the way
When looking at a BI solution it is important to take a holistic view of what you are trying to achieve and the key ingredients in the solution. Here are some important considerations:
Guided analytics and distributed reporting or self-service analytics.
Is a mobile solution required?
Existing applications and business systems.
User skill levels / Experienced developers, business users or both.
Security.
Data / Access / Quality / Volume.
Time to value.
Maintenance - BI solutions often require ongoing development and support.
Cost.
Cost needs to be looked at closely, and we mean the total cost of the software, consulting services and training to get a result. It is important to consider ongoing maintenance of the system. It is common for management to ask for further information, new reports, calculations, different formatting and inputs from additional systems.
One BI tool may offer better performance but if it is 10x the cost of its rival and the implementation and support costs are much higher, it will be a difficult business case to justify, unless there is some critical feature like security for regulatory compliance that is a non negotiable requirement. Qlik is very strong in security, backed up by its use in the finance industry by clients like Westpac and ANZ.
Qlik is a market leader in BI, with close to 50 000 customers globally. Let’s take a look at Qlik’s recent announcement about dual-use licencing and a short history of their BI tools.
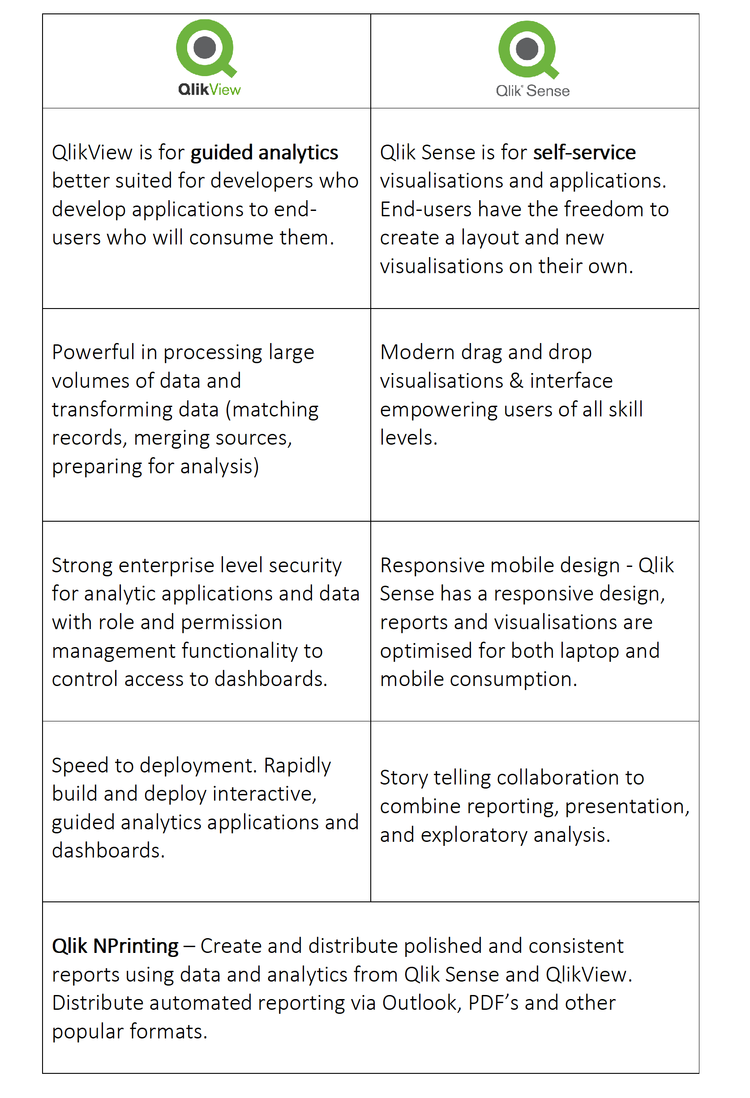
Dual-use licensing means you can get Qlik’s modern platform – Qlik Sense: Simple, intuitive and visually brilliant and the original – QlikView: Versatile, complex and powerful. This is an interesting offer for existing users and anyone looking at implementing a BI platform.
Dual-use licencing allows companies to unlock both QlikView and Qlik Sense with a single license key.
The cost is a 30% uplift in annual Qlik maintenance. (*Qlik press release)
This is good news for existing Qlik customers offering access to both products at an additional cost.
Dual-use licensing offers customers a more complete BI offering for both guided and self-service analytics.
Qlik: Our Experience.
We compared many BI platforms when looking at better insights into our own managed services and consulting business as well as offering the service to our clients. Tableau was seriously analysed and considered, and very compelling with a lower cost to get started and great design. After many comparisons, we found Qlik was a better fit for us, more powerful and its ETL (extract transform load) capability was simply better. Tableau is a great tool with some of the best visualisations available. With Qlik, you can pull data from many different sources without the need for a costly data warehouse. Here at Advance, Qlik is one of the main tools we use when developing BI solutions internally and for our clients, Power BI is another key tool with its strengths and a high adoption in the BI arena.
Qlik really is one of the most powerful tools available and difficult to beat when comparing its ability to handle large data volumes and transforming data (matching records, merging sources, preparing for analysis.) QlikView is a genuine enterprise level BI tool.
Our experience with QlikView:
Ease in connecting to virtually any data source.
We are technical developers - QlikView is very powerful in its ability to manipulate or transform the data structure by using script statements and expressions in the Qlik load script.
Speed in building and delivering powerful insights right away. Even in product demonstrations we were able to connect to the data and build dashboards instantly.
Time to value can be as low as a few days.
Limited mobile experience with QlikView - We eventually built our own in house application to give us a better mobile experience and additional capability like distributed reporting and Excel integration through KPI Pulse.
A Short History Of QlikView And Qlik Sense. Why Two Products?
QlikView
Qlik Sense
QlikView has been the flagship product from its founding in the early 1990s through to around 2014, when they introduced Qlik Sense. Since the launch, Qlik has arguably spent more of its development resources on Qlik Sense, a mobile responsive and more visually appealing BI tool. With that said, the 30 000+ QlikView user community has ensured Qlik release new versions of QlikView annually. Some speculate the move towards Qlik Sense might be to better compete with modern and visual data exploration platforms like Tableau.
From our experience, QlikView developers like us find it easier to get results straight away using QlikView when compared to Power BI and Qlik Sense. Important insights with drill down capability right away. QlikView may not look as visually appealing out of the box as Qlik Sense, but more experienced developers can get complex answers quickly, then make them more presentable for public consumption.
Users coming from a programming or data science background are more likely to find QlikView more flexible and powerful. In contrast, for brilliant looking visualisations and self-service analytics - Qlik Sense shines in this area and the mobile experience is responsive meaning that the platform automatically resizes objects. This is important when working across different platforms like mobile phones and tablets, all with different versions of operating systems. Qlik Sense wins here in delivering a modern mobile experience.
Key Differences And Strengths Of Each Product.
Final Thoughts
Qlik offers a leading BI solution and dual-use licensing is a good thing. It highlights that they want to offer more value in this competitive space and they need to. Power BI offers a comparatively low entry cost and provides a very good BI platform. You can read some of the reasons why we have seen a big spike in demand for Power BI here. Is Qlik the right solution for you? It is a powerful tool but definitely not the lowest cost option.
A thorough analysis of the project needs to be undertaken. Experienced BI experts can provide advice on which tool is a good fit based on outcome required with budgets and total cost in mind. This will help you make an informed decision on the right platform for your business.
Qlik’s new licencing offering is an interesting proposition for anyone looking at a implementing a BI platform. Current users of QlikView can continue developing and supporting existing deployments and try newer features in Qlik Sense for a lower cost than purchasing two seperate tools. This move will also grow interest and additional enquiries for Qlik.
If you are an existing user of Qlik or someone looking to tackle a new BI project, it is a great time to take a serious look at Qlik. There a many great BI platforms out there, Tableau and Power BI are also leading offerings and each has its strengths that really need to be considered and aligned to your business and what you are trying to achieve.
Want To Know More?
You can reach us here or email sales@advance.on.net directly with any queries. BI is our passion and expertise.
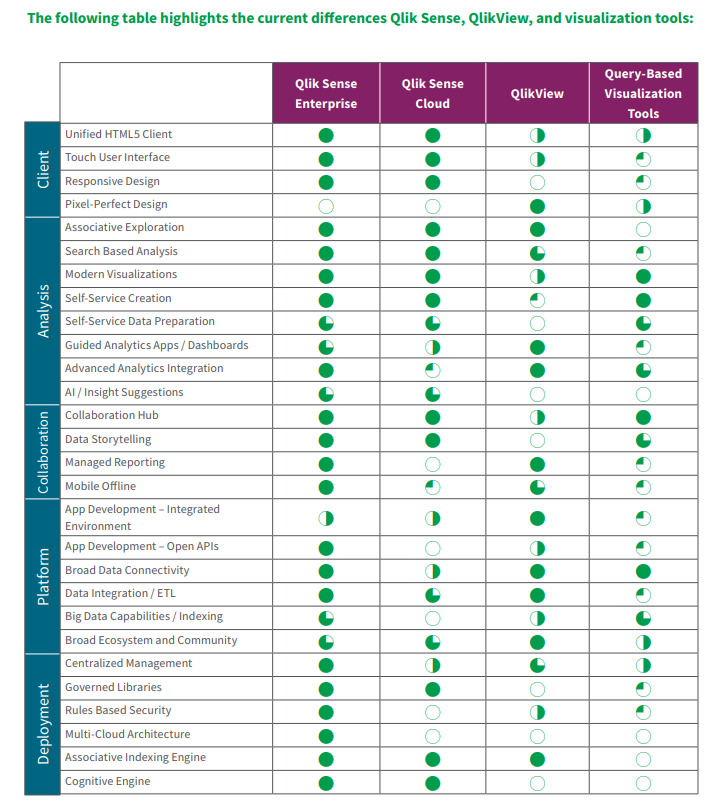
We’ve included links to additional content and useful comparison in the Qlik datasheet below.
Additional Insights
Below is a great 5 minute video about Qlik’s April 2019 updates.
Qlik Sense and QlikView Data Sheet PDF
Many Thanks,
John-Paul Della-Putta
Director
Phone: +61 8 8238 6500
Email: jp@advance.net.au
LinkedIn: www.linkedin.com/in/johnpaul
Website: www.advance.net.au
Antivirus Software and Firewalls
Antivirus Software and Firewalls
These days almost everyone uses the internet on a regular basis, whether at home, work or on the go. The internet is a tremendously valuable resource; as the number of people accessing the internet grows, so do the risks associated with it. Regardless of whether you are accessing the internet for personal or professional purposes, it is imperative to ensure you are doing so safely.
Two vital components to protect yourself and your system online are an effective anti-virus and a firewall.

Antivirus software
Anti-virus software is your primary defense against malicious threats online and offline. An anti-virus runs in the background of your computer, quietly checking every file that is accessed, monitoring for threats (this is often referred to as ‘real-time protection’). Your anti-virus runs these files through its database, checking against known viruses and other malware. Because of this method, it is very important that you regularly check for updates with your anti-virus software or set it to auto-update.
Anti-virus software can also perform a ‘full system scan’, where it will scan the selected locations to ensure there is no malware lying dormant. Full system scans are typically used when initially installing the software, or when you think your computer is acting up and something could have slipped through the cracks of your real-time protection.
Firewalls
In the most basic sense, a firewall is a barrier to keep damage away from your property – hence the name firewall. A firewall is a piece of software or hardware that sits between your computer or private network and the internet. Its job is to filter information (packets) coming through your connection, and if need be, reject them. A firewall gives you several options to establish rules to identify the traffic allowed in and out of your network, whether restricted by IP, certain ports or through application filtering amongst others.
By rejecting this unwanted traffic, the firewall prevents those with malicious intent being able to probe your network and attempt to cause damage by stealing information, uploading malware, performing denial of service attacks, using remote login, source routing and more.
Firewalls are effective at protecting your system from unauthorized entry, but they are not capable of removing malware from an already infected system – therefore firewalls should always be used in conjunction with some form of anti-virus software, ensuring that both are always up to date.
For more information on Managed Technology and Security please contact us
{{cta('dd78255c-b081-4f2e-a8c9-5a78a80cbed1')}}
How Important Are Windows Updates?
We’ve all seen the notifications for when Windows Updates are available, and I’m sure most of us have thought to ourselves “Again?! I only just installed one last week!”.
Have you ever thought to yourself why they pop up at what seems to be the most inopportune moments, and with such importance?
What is a Windows Update?
Windows Update is an inbuilt Microsoft service used for periodic updating of system files, to patch known issues and vulnerabilities with Microsoft products. This includes the Windows OS itself, Microsoft Office, Microsoft Edge, etc.
Each Microsoft Update is assigned an associated Knowledge Base number (KB) which gives further information on the updates. Updates are classified as one of four types:
Critical Updates
- These fix major issues, found across all Microsoft Products, that cause errors or unexpected functions. Alongside Security Updates, these are the highest priority updates to apply and should be done as soon as possible.
Security Updates
- Security Updates are applied to address security vulnerabilities which can allow a system to become compromised. Security updates have five different levels of importance; Critical, Important, Moderate, Low or non-rated. Security updates classed as Critical are the most important updates for your system and ignoring these can leave your server or computer vulnerable to hackers and other malicious attacks.
- Security updates are provided with a Microsoft Security Bulletin number (MS) for further details.
Software Updates
- Applied to cover non-critical problems, often applying feature updates and addressing minor bugs.
Service Packs
- Service packs are an amalgamation of all updates up to a certain date, for a specific piece of software or operating system, typically including feature updates.

How can I ensure that my systems are secure?
All recent Microsoft Operating Systems have in-built automatic updating features, which allows you to schedule and download high-priority updates.
If you are managing multiple desktop computers and even servers, the most efficient and effective way to stay up-to-date is to offload what can be a mammoth task to a Managed Service Provider (MSP). Managed Service Providers employ professionals with years of experience maintaining, reviewing and applying Microsoft patches to a vast range of different environments.
Using monitoring software MSP’s are able to monitor patch statuses remotely and schedule regular patching cycles to ensure that all critical and relevant patches are applied as soon as they are available. If issues are to arise from any patches pushed by Microsoft, your MSP is able to analyse the issue and determine which patches can be causing the issue and disable them, or roll-back where necessary.
By removing the burden of responsibility internally and placing it in the hands of experienced professionals, you can rest easy knowing that your systems are receiving the best in pro-active care.
If you are interested in what Advance can offer in this scope, please don’t hesitate to get in touch.
Which Backup Media Is Right For You?
Twenty years ago, backup media was easy to get your head around. Floppy Disk, Iomega, CD and Tape Drives, nothing to it.
Nowadays there’s so much more – what method of backup to use, where the backups are stored, how the backups are taken, when they are taken and how the backups are tested to ensure they are restorable.
Floppy disks and Iomega have gone the way of the dodo, but let’s look at current backup media still in use
- USB Stick
- Internal Hard Drive (via RAID)
- External Hard Drive
- NAS
- CD / DVD (some people still use it!)
- High Speed Tape Drives
- Remote Backup Services
- Syncing over internet (OneDrive, Google Drive etc.)
- Cloud Backup
Each of these methods has its place depending on many factors, but don’t fool yourself thinking that a cheaper version will be ‘OK’ - It rarely is.

Considerations when deciding on a backup media type
Type of backup
Whether you are backing up hourly or daily and what sort of files you are backing up should help determine what backup media to use. For example, if you have a large amount of data requiring a nightly backup, then you could not use DVDs.
Backup Media Cost
It is important to factor in the cost of backup media, as well as the number of devices you require to ensure a consistent and effective backup process.
Backup data security
Identifying what is backed-up and how sensitive that data is can help you decide the most appropriate backup media. If your data is integral to your business, don’t sacrifice quality for savings.
Restorability
You need to weigh the risk of your selected media - how often will a restore fail per 1000 times it is tried? Each type of backup media has its own pros and cons and you need to investigate them properly to make an informed decision.
Hardware Redundancy
Ensuring that your hardware is not going to become redundant over time is extremely important when choosing a media type. Five years down the line, you may need to restore data which seems recent today, and the hardware may be considered obsolete with the restore devices hard to find. Restoring from a 3.5” floppy disk today would not be the easiest task.
Restore speed and time
Depending on the data, whether it is ‘mission critical’ or whether you can do without for a day or more, all plays a part on which backup media to use and what processes to put in place. Consider putting your crucial servers on a quicker restoring media where possible.
These are only a few considerations when looking at backup media. You need to see the complete picture and envision where your organisation might be in five to ten years’ time. If you think back on how things have changed since the 1990s, you can appreciate that being open to new ideas and processes could not only save you time, but also money.
For more information on back-up software and processes, get in touch with one of our highly experienced staff today.
{{cta('dd78255c-b081-4f2e-a8c9-5a78a80cbed1')}}
Are Your Business Processes a Target For Scammers?
Cyber criminals are tricking CEOs out of millions of dollars by exploiting their organisations poor business processes and fooling unsuspecting employees into transferring money. The growing trend, known as ‘CEO Whaling’, involves plain text e-mails being sent to employees’ responsible financial transactions, masquerading as their boss requesting them to urgently pay invoices. Those falling victim have no way to recover the money with insurance generally not covering international fraud.
These highly organised con artists are not just spamming companies at random, instead they’re using social media to research potential victims, taking advantage when they’re most vulnerable. For example they may identify through social media that the boss or the person responsible for financial transfers is on a holiday and that’s when they strike, sending an e-mail saying they’re about to get on a flight and need an invoice paid urgently. They use a fake e-mail address and include some personal details uncovered via social media to give the e-mail just enough validity to trick the employee into believing it needs to be done and that requesting confirmation will probably make their boss angry due to the delay caused by being on a flight and unable to respond.

Organisations with business processes that rely on an e-mail from the boss for financial approvals are at high risk of falling victim to this scam as the process doesn’t include any validation that the invoice hasn’t been modified or that the approval has come from the person with authority to approving it. Busy people find the use of e-mail in a process like this convenient as they can be sent at will from virtually anywhere, on any device, at any time, putting them at risk of being exploited. Processes that involve printing, stamping, signing and shuffling paper around for approval stall when the approver is not in the same location as the document. Allowing e-mails to be used in place of an actual signature on the document makes the process susceptible to scammers. This issue was recently reported on in The Advertiser, read that article here http://www.adelaidenow.com.au/technology/how-australian-bosses-are-being-tricked-out-of-millions-of-dollars-by-cyber-criminals/news-story/57318e06c02a8215b8d67d521a219aea.
The solution to avoid being tricked by the scammers is to implement a flexible solution like M-Files where the business process is migrated into the system with secure access provided via desktop, web and mobile app. M-Files stores a single electronic version of the invoice with security that restricts access to only the people involved. This avoids copies of the invoice being e-mailed, instead those involved all refer to the same version stored in M-Files. With the approval process managed via workflow, the approver is notified of an invoice to approve and is required to authenticate themselves to view and approve, which can be done quickly a simply via the mobile app using fingerprint authentication. The people responsible for payment are then notified and required to authenticate to access the approved invoice. M-Files keeps a detailed version history of every change the document goes through, so if the person responsible for payment wants validation that the boss approved the invoice for payment, they can review the documents history to confirm it was actually approved by the boss’s user account. The version history can be used to identify changes to the original document and can potentially identify fraud attempts where bank details for payment have been changed on an invoice. Aside from not falling victim to fraud, the benefits of keeping the records electronically rather than physically include incredibly fast retrieval of information and increased office space when you recycle the filing cabinets for scrap metal.

If you’re still using a manual process that involves printing, stamping, signing and shuffling paper around your organisation for approval that can be short circuited by e-mails, you are at risk of being scammed. If you think it won’t happen to you, think again as the Federal Government have been briefed on the severity of this trend because the losses are increasing into the millions. If you want to know more about how M-Files can help your business, please contact us.
5 Public Cloud Myths Exposed
The public cloud is a hot topic in IT today. Even though it has been around for about ten years, cloud offerings from AWS, Azure and Google cloud have made the public cloud more mainstream and easier to get onto. In some instances though companies are jumping on board without really understanding it. So in an effort to debunk some myths here are five myths to consider if you are contemplating moving to the public cloud:
1. Public Cloud is Cheaper
The AWS/Azure public cloud “pay by use” methodology was a huge game changer for companies jumping onto the pubic cloud, but there is an assumption that “pay by use” will automatically make the subscription cheaper.
It can in some instances, but it should be noted that in many cases High Availability environments will usually come out cheaper with a hosting provider rather than a public cloud option. Data out transfer costs and dedicated resource costs both come into play in a big way in a High Availability environment, and things can get very expensive, very quickly. Many companies have tried out the public cloud and have gone back to dedicated resources in a managed cloud where the investment is more reasonable and consistent.
2. Everything should go to the Public Cloud
Due to the time it can take to tailor your application to the public cloud (not all applications are really built for the cloud/virtualization, much less the public cloud), not all companies environments are sitting in the public cloud. You really need to have an in-depth discussion with your IT Provider to determine what can be in the public cloud and what should be in the public cloud.
3. Full Security/Compliance Comes with Cloud Infrastructure
Security is much better in the cloud today than it has been in years past. Even though public cloud offerings like AWS and Azure offer HIPPA or PCI compliant solutions, it does not mean that will automatically make you compliant on moving to the public cloud. The infrastructure they provide to you is compliant, but once you configure your application on top of it, it becomes a completely different story.
4. Moving to Public Cloud is Simple
Some applications can be moved to the cloud simply, however putting a full environment that has not been configured and is technical within itself is a different story. Use your IT Provider or someone with the right expertise and experience to migrate the environment as it can get complicated quickly and without a good foundation getting your application to work on top of it may end up being expensive.
5. Managing the Public Cloud is Simple
Once someone has designed, built and migrated your application to the public cloud, it should be simple to manage from there – surely? You would think so but it is not the case! You really need to have your IT Provider work on maintaining, tweaking and scaling the configurations to keep your cloud “humming” along.
The simple suggestion here is to let the experts build, migrate and manage it for you. Cutting corners in the public cloud will come back to bite you.
For more information on Cloud & IT Services click here